Ransomware attackers are shifting their focus to critical businesses and industries more likely to pay, and double extortion tactics
A new annual cybersecurity report by Trend Micro highlights the growing rate of cyberattacks in the UAE by malicious actors on digital infrastructures and individuals in the modern-day hybrid work environment. The report states that globally Trend Micro solutions stopped over 94.2 billion threats in 2021, a 42 per cent increase in the number of detections recorded in 2020. Attacks had surged over 53 billion in the second half of 2021, blocking 41 billion threats in H1. Ransomware attackers are shifting their focus to critical businesses and industries more likely to pay, and double extortion tactics ensure that they can profit.
Ransomware-as-a-service offerings have opened the market to cybercriminals with limited technical knowledge and given rise to more specialisation, such as initial access brokers, who are now an essential part of the cybercrime supply chain. Threat actors are better at exploiting human error to compromise cloud infrastructure and remote workers. Homeworkers are often prone to take more risks than those in the office, making phishing a greater risk.
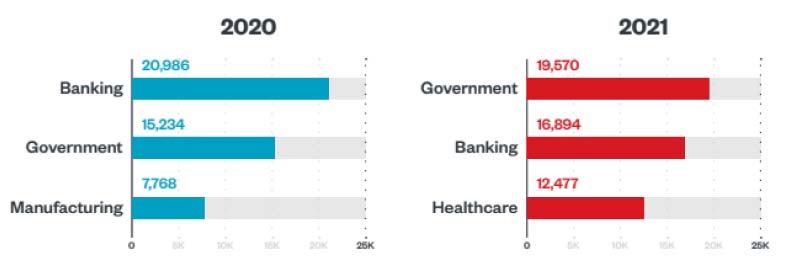
Notably, in 2021 ransomware operators staged attacks on more profitable targets, leading to business disruptions with real-world ramifications felt on a global scale. Already strained by the pandemic, healthcare organisations were hit hard by ransomware attacks in 2021, which were just behind the banking and government industries regarding ransomware detections.
The report suggests that because healthcare organisations are less likely to back up their data than those in other industries, they are more prone to paying the demands of ransomware actors. Moreover, the healthcare industry has a trove of data that attackers seek to sell or use for extortion, including patient records with social security numbers, medical histories, and financial information.
The widespread use of RaaS results from the ongoing evolution of the flourishing cybercrime-as-a-service market, which continues to develop new business models for attackers. One such development is the growing demand for access-as-a-service (AaaS), with access brokers peddling stolen credentials in the criminal underground and finding reliable customers in ransomware actors who use their wares to infect target systems.
In the UAE, Trend Micro solutions detected and blocked over 31.6 million email threats, more than 5.4 million malware attacks, and nearly 36 million URL victims’ attacks. Furthermore, shielding remote learning and working, Smart Home Network (SHN) solutions protected devices and networks from over 15.7 million SHN inbound and outbound attacks and prevented over 5.4 million SHN events.
“While the UAE’s enterprises appear to be on the recovery after successfully weathering recent crises such as the pandemic and other global events, cybercriminals have shown no signs of slowing down their sophisticated attacks. Moreover, the challenges of hybrid work, remote locations, and company-issued remote devices have led enterprises to reapproach their security strategies to protect against newer vulnerabilities. The Trend Micro annual cybersecurity report provides insights on the current threat landscape and serves as a guide for organisations to protect their digital ambitions with multilayered security solutions for a better tomorrow,” said Majd Sinan, Country Manager, UAE for Trend Micro.
Threats to cloud security were among the most pressing IT infrastructure risks for organisations. Protecting their cloud architecture is a challenge for companies because many of the technologies that compose this architecture are regularly updated with new features. Besides these complexities, defenders must keep up with the tools malicious actors use to target the cloud, which is also constantly changing.
Fortifying the security postures of cloud environments that use services like those of Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP) should be a top priority for cloud adopters, for whom misconfigurations might not only lead to costly data breaches but also run up expenses from idle instances and unused storage.
If you liked reading this, you might like our other stories
Building The Cognitive Enterprise
Google Doubles Down On Language Model At Google I/O









