The insights shine a spotlight on a rapidly expanding identity problem and explore perspectives on the evolving threat landscape
A new global report on the 2022 Identity Security Threat Landscape by CyberArk identifies how the rise of human and machine identities, often running into the hundreds of thousands per organisation, has driven a buildup of identity-related cybersecurity “debt,” exposing organisations to greater cybersecurity risk. The report shows that 79 per cent of senior security professionals state that cybersecurity has taken a back seat in the last year in favour of accelerating other digital business initiatives
The findings were gathered from a worldwide survey of 1,750 IT security decision-makers, highlighting their experiences over the past year in supporting their organisations’ expanding digital initiatives. Insights from the same shine a spotlight on a rapidly expanding identity problem and explore perspectives on the evolving threat landscape.
It also directly links rampant cybersecurity debt and imbalanced investment decisions that emphasise digital projects over robust security measures. The gap has been a significant issue for organisations in 2022: identities being a prime attack vector and waiting to apply security controls after an attack is not a responsible security policy.
According to survey results, the number of digital identities in organisations is already remarkably high and will continue to grow in parallel with high-priority initiative rollouts. In a typical enterprise today:
- The average staff member accesses more than 30 applications and accounts
- Machine identities outnumber human identities by a factor of 45x
Some identities provide direct, privileged access to sensitive data and assets, so people and machines can perform their jobs or functions. All identities can become privileged under certain conditions, based on the systems, environments, applications or data they are accessing, or the types of operations they are performing. This seems to be the reason why it is critical to manage and secure all identities and why it can be difficult to do so as new ones are generated rapidly.
In most organisations, the number of people and machines with access to sensitive data is already high:
- More than half (52 per cent) of organisations’ workforces have access to sensitive corporate data on average
- 68 per cent of non-humans or bots have access to sensitive data and assets. It takes just one compromised identity for an external or inside threat actor to start an attack chain. The acceleration of digital initiatives and the resulting surge in digital identities feed into an expanding attack surface.
Security professionals agree that recent organisation-wide digital initiatives have come at a price. This price is Cybersecurity Debt; while security programs have expanded, they have not kept pace with organisations’ investments focused on driving business operations and growth. This debt has arisen through not properly managing and securing access to sensitive data and assets, and a lack of Identity Security controls is driving up risk and creating consequences. The debt is compounded by the recent rise in geopolitical tensions, which have reinforced the need for heightened awareness of the physical consequences of cyber attacks, especially on critical infrastructure.
“Spending on digital transformation projects has skyrocketed in recent years to meet the demands of changed customer and workforce requirements. The combination of an expanding attack surface, rising numbers of identities and behind-the-curve investment in cybersecurity – what we call Cybersecurity Debt – is exposing organisations to even greater risk, which is already elevated by ransomware threats and vulnerabilities across the software supply chain. This threat environment requires a security-first approach to protecting identities, one capable of outpacing attacker innovation,” said Udi Mokady, Founder, Chairman and CEO, CyberArk.
Potential Solutions
- Push for transparency: 85 per cent say that a Software Bill of Materials would reduce the risk of compromise stemming from the software supply chain.
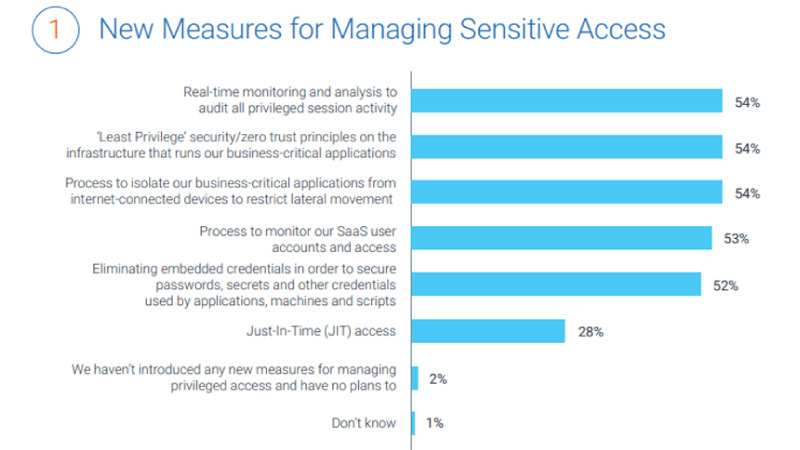
- Introduce strategies to manage sensitive access: The top three measures that most CIOs and CISOs have introduced (or plan to introduce), each cited by 54 per cent of respondents: real-time monitoring and analysis to audit all privileged session activity; least privilege security/ zero trust principles on infrastructure that runs business-critical applications; and processes to isolate business-critical applications from internet-connected devices to restrict lateral movement.
- Prioritise identity security controls to enforce zero trust principles: The top three strategic initiatives to reinforce zero trust principles are: workload security; Identity Security tools; and data security.
If you liked reading this, you might like our other stories
Build A Strong Data Protection Strategy In 10 Steps
When It Comes To Cyber Threats, All Roads Lead To Identity









