Kaspersky researchers recently uncovered a new malicious WhatsApp spy mod, proliferating within another popular messenger, Telegram.
Users often use third-party mods for popular messaging apps to add extra features. However, while enhancing functionality, some of these mods also come with hidden malware. Kaspersky has identified a new WhatsApp mod offering not only additions like scheduled messages and customisable options but also contains a malicious spyware module.
The modified WhatsApp client’s manifest file includes suspicious components (a service and a broadcast receiver) not present in the original version. The receiver initiates a service, launching the spy module when the phone is powered on or charging. Once activated, the malicious implant sends a request with device information to the attacker’s server. This data covers IMEI, phone number, country and network codes, and more. It also transmits the victim’s contacts and account details every five minutes and is able to set up microphone recordings and exfiltrate files from external storage.
The malicious version found its way through popular Telegram channels, predominantly targeting Arabic and Azeri speakers, with some of these channels boasting nearly two million subscribers. Kaspersky researchers alerted Telegram about the issue. Kaspersky’s telemetry identified over 340,000 attacks involving this mod in just October. This threat emerged relatively recently, becoming active in mid-August 2023.
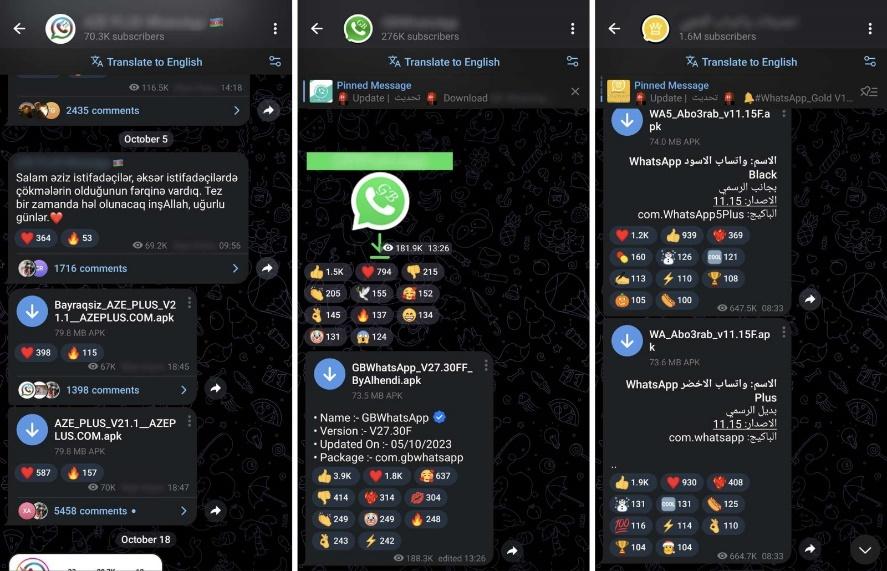
Source: Examples of Telegram channels distributing malicious mods
Azerbaijan, Saudi Arabia, Yemen, Turkey, and Egypt are the top 5 countries with the highest attack rates. While the preference leans towards Arabic and Azerbaijani-speaking users, it also impacts individuals from the US, Russia, UK, Germany and beyond.
Kaspersky products detect the Trojan with the following verdict: Trojan-Spy.AndroidOS.CanesSpy.
“People naturally trust apps from highly followed sources, but fraudsters exploit this trust. The spread of malicious mods through popular third-party platforms highlights the importance of using official IM clients. However, suppose you need some extra features not present in the original client. In that case, you should consider employing a reputable security solution before installing third-party software, as it will protect your data from being compromised. For robust personal data protection, always download apps from official app stores or websites,” comments Dmitry Kalinin, a Security Expert at Kaspersky.
To stay safe, Kaspersky experts recommend:
- Use Official Marketplaces: Download apps and software from reputable and official sources. Avoid third-party app stores, as the risk they may host malicious or compromised apps is higher.
- Use reputable security software: Install and maintain reputable antivirus and anti-malware software on your devices. Regularly scan your devices for potential threats and keep your security software current. Kaspersky Premium protects its’ users from known and unknown threats.
- Educate yourself about common scams: Stay informed about the latest cyber threats, techniques, and tactics. Be cautious of unsolicited requests, suspicious offers, or urgent personal or financial information demands.
Third-party software from popular sources often comes with zero warranty. Remember that such apps can contain malicious implants, e.g., because of supply chain attacks.









