Trend Micro released its 2020 Annual Cybersecurity report: A Constant State of Flux with special focus on how the pandemic and the pandemic-induced lockdowns impacted cyber-security threats for enterprise.
Targeted ransomware continued to be a major concern. Older ransomware families such as Ryuk sustained their attacks on organisations, while newer ransomware such as Egregor and DoppelPaymer conducted highly damaging operations in 2020.
In the UAE, Trend Micro detected and blocked over;
- 19 million (19,662,122) email threat
- prevented 10 million (10,304,154) malicious URL Victim attacks,
- 119,000 (119,724) URL hosts.
- 2.7 million (2,744,886) malware attacks were identified and stopped
- 1,600 (1,635) online related banking malware threats were blocked
Attacks were often launched on critical industries at the forefront of the fight against the Covid-19 pandemic, such as healthcare, government, and manufacturing, according to the Trend Micro report.
Despite the use of increasingly complex campaigns by threat actor groups, phishing remained a widely used strategy, owing both to its simplicity and to its effectiveness. Social engineering techniques hardly remained static, however, and saw constant, if small, evolutions over the past year.
The report also shows that home networks in the UAE were a major draw for cybercriminals looking to pivot to corporate systems, devices, and networks. Across the emirates, Trend Micro’s Smart Home Network (SHN) solutions blocked more than 25 million SHN Inbound and outbound attacks combined, preventing 13 million (13,308,205) such SHN events for hackers to target or control home devices from executing malware, obtaining sensitive information, intercepting communications, or launching external attacks.
In its efforts to ensure secured digital transformation journeys of organisations in the UAE, Trend Micro has been working closely with public and private sectors to create awareness and bridge the gaps. Earlier this year, the company launched its Trend Micro Vision One platform to empower security teams in adopting a new approach that goes beyond – to provide enhanced visibility, threat intelligence, with extended detection and response at every layer of their IT environments.
According to the report, the top 10 malware families in terms of detections in 2020 included familiar names, with WannaCry, Coinminer, and Emotet making up the top three.
While Windows-based operating systems still make up the majority of machines that were detected to have some form of malware infection, a sizable number of macOS and Linux machines also suffered similarly.
Here is what we learned from the report regarding major shifts in cybersecurity triggered alongside the Covid-19 pandemic and move to remote working environments;
Malicious Actors Take Advantage of Global Pandemic
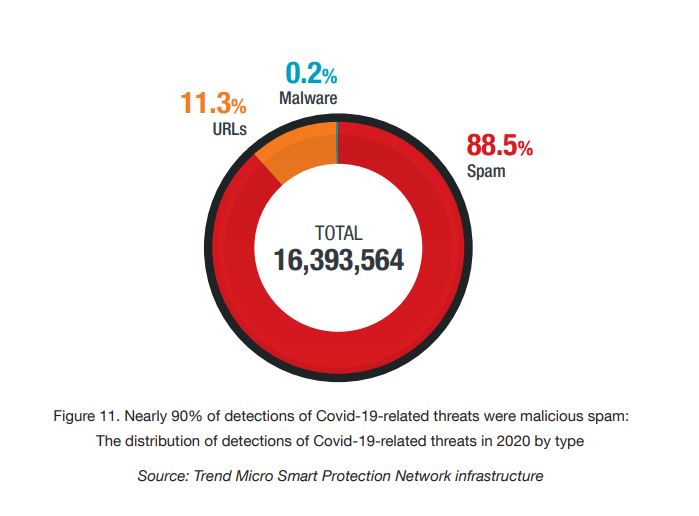
In 2020, Trend Micro detected more than 16 million Covid-19-related threats, consisting of malicious URLs, spam, and malware. Nearly 90 per cent of these detections were malicious spam. This indicates that spam emails were the preferred avenue for malicious actors, likely because of their accessibility and simplicity relative to malicious URLs and malware, which require some technical knowledge and planning. The bulk of these detections came from the US, Germany, and France, which were also among the countries that had been hit hardest by the pandemic.
In the first half of the year, Covid-19-based threats focused on either causing alarm to recipients or allegedly providing information about the pandemic. The scammers behind these threats tailored their techniques to whatever new and current information was available.
The initial rollout of Covid-19 vaccines from different drug companies in the second half of the year triggered a new set of attacks. Some offered fake vaccines for varying amounts, even setting up domains (some of which included malware) to fool their victims. Other scammers resorted to phishing emails, sent not just to the general populace but also to people involved in the vaccine supply chain.
Business email compromise (BEC) scammers also banked on the pandemic, as Covid 19-related subject lines made up the highest number among the BEC samples we detected. Many of the subject lines were vague, with some even referring to unrelated topics such as invoice or payment requests. However, even these emails found a way to use the terms “Covid” or “Covid-19,” likely as a way to garner their victims’ attention.
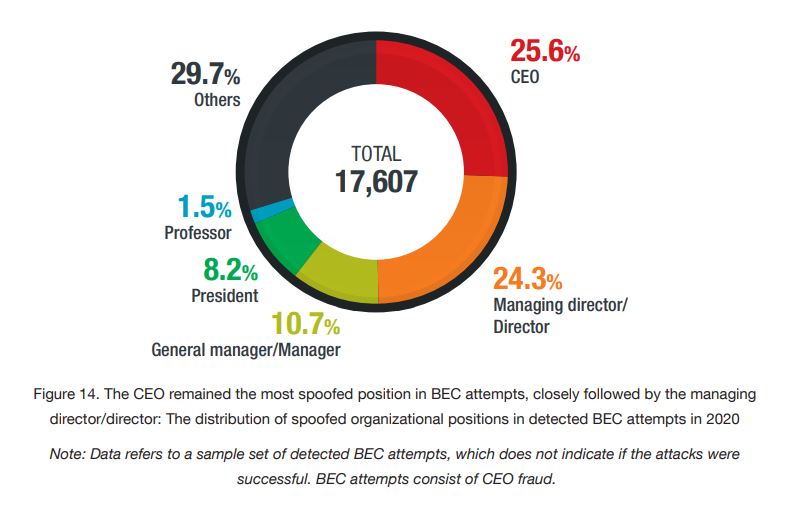
Overall, however, the number of BEC attempts detected in 2020 decreased by 17 per cent year on year from 2019.
One of the hallmarks of BEC attacks is that its perpetrators do not need to have a complex infrastructure to pull off successful attacks. Scammers can even use public cloud infrastructure, as observed in the Water Nue BEC campaigns. This series of campaigns, which started in March 2020, targeted senior executives in the US and Canada to obtain account credentials for further malicious activities. Once compromised, these accounts were used to send fund transfer requests to lower-ranking staff. The fraudsters behind Water Nue used legitimate cloud-based email services such as SendGrid to deliver their emails. Water Nue campaigns collected more than 800 credentials at the time of the report.
Remote Work Presents Challenges for Organizations
The transition to remote work also led to increased reliance on communication tools such as Zoom, Slack, and Discord. This, in turn, led to an increase in attacks that targeted or used these applications. “Zoombombing,” in which unwanted users would intrude on ongoing Zoom meetings, was one of the more common methods of communication app abuse. And while it could be highly disruptive at times, ultimately most instances of Zoombombing amounted to nothing more than harmless, if annoying, pranks.
Other types of Zoom-related attacks, though, were more damaging. Some malicious actors resorted to using Zoom installers — either legitimate ones bundled with malware or malware disguised as installers — to trick users into installing various payloads on their machines. Slack and Discord were also incorporated by cybercriminals into their attacks. One of these involved Crypren, a ransomware variant that had a unique method of reporting its victims’ encryption status back to the command-and-control (C&C) server: via Slack webhooks.
Cloud Misconfiguration Still a Problem for Many
The improper configuration of cloud infrastructure is often overlooked by organisations leaving them open to threat. The report observed that attackers looked for open APIs to exploit. In April 2020, it was reported that attackers had dropped cryptocurrency miners on misconfigured Docker daemon API ports via the Golang-based Kinsing malware. One notable characteristic of Kinsing is its ability to hide the presence of malicious components through the use of a rootkit, making its activities difficult to detect for affected users.
Attacks on IoT Devices Increased
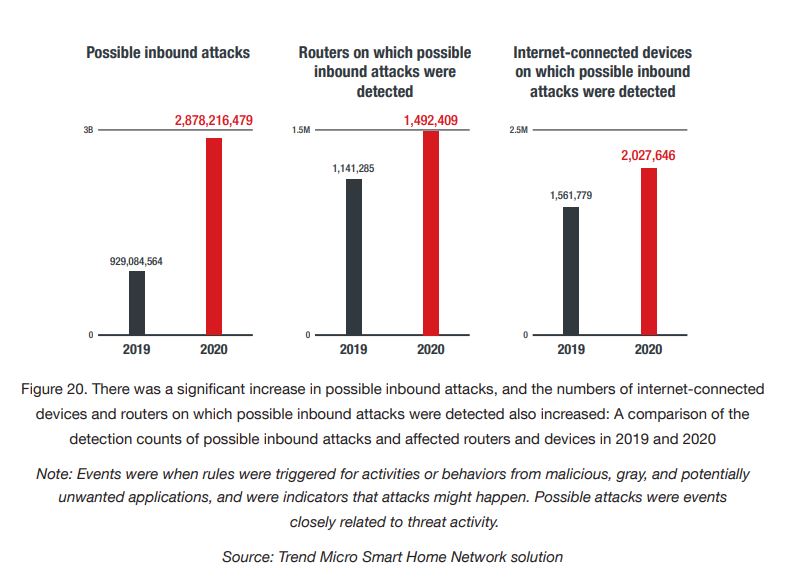
Compromised home networks and devices serve as launching points for attackers to jump to other devices connected to corporate networks. Routers are particularly vulnerable especially since the security at an employee’s home is not as robust as that at an enterprise workplace. Based on Trend Micro data, inbound attacks occurred on 15.5% of routers while 5.1% of routers were used for outbound attacks in 2020.
In the past year, we also saw an uptick in the total number of inbound attack events, which was more than triple the 2019 tally, and in the total number of outbound attack events, which nearly doubled from 2019.









